Storage with AWS S3
This guide describes how to create a bucket in Amazon S3. You can use the bucket with Axinom Encoding as an input and/or output storage.
To create an AWS bucket:
-
On the s3 AWS Console, click create bucket.
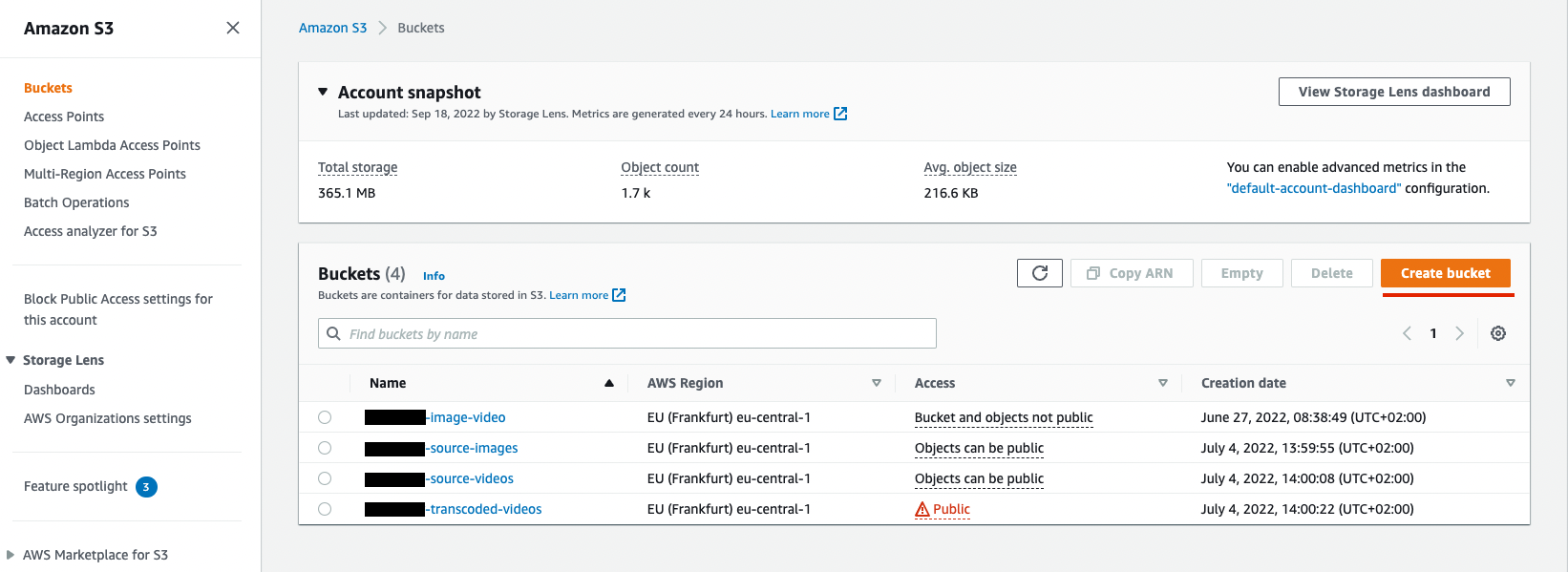 Figure 1. Start creating a bucket
Figure 1. Start creating a bucket -
During the bucket creation you should use unique name, proper AWS region and deselect all
Block all public access, agree the acknowledge of the public access and create the bucket.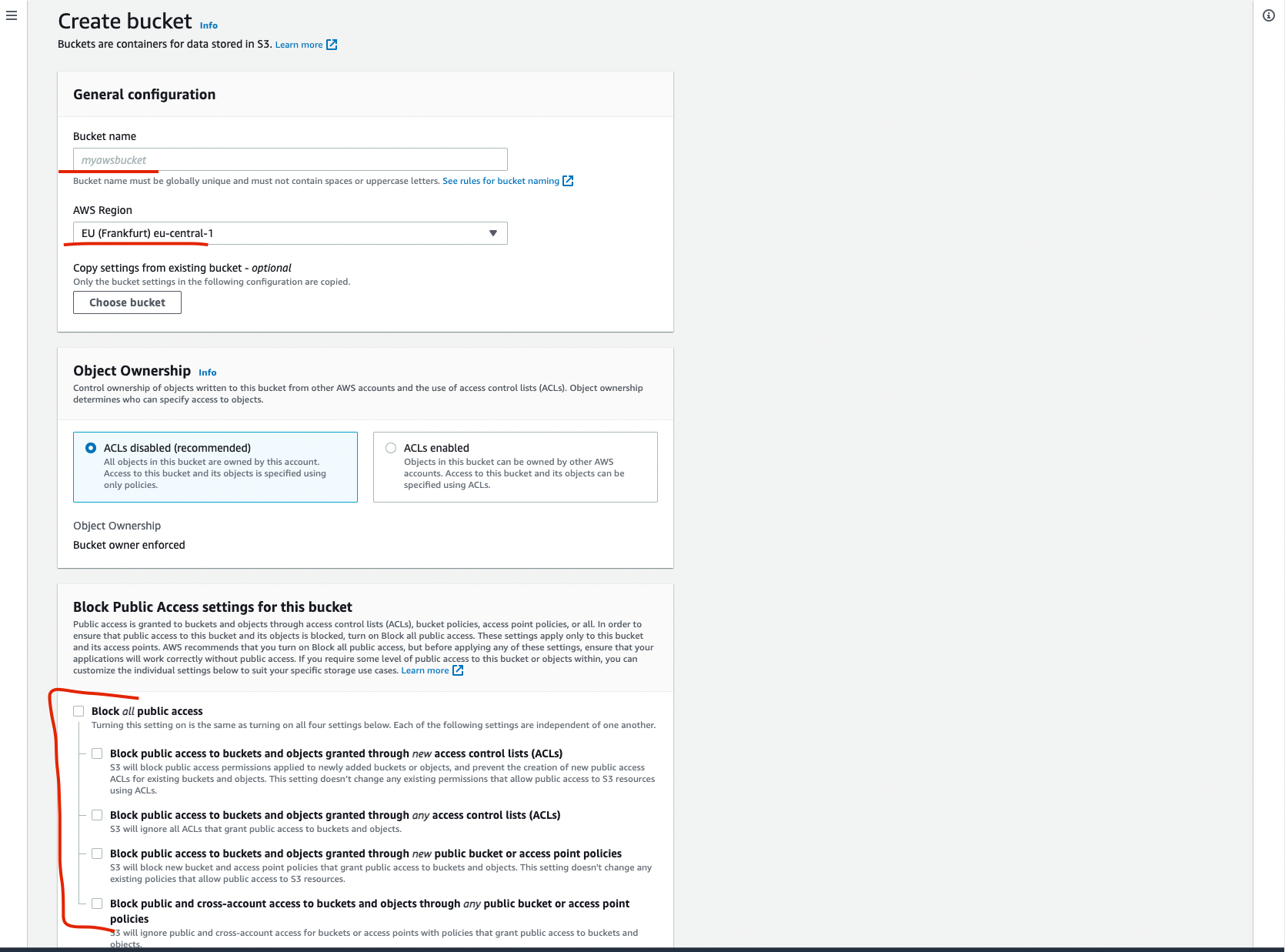 Figure 2. Bucket initial settings
Figure 2. Bucket initial settings -
Created bucket is not public yet. To make it properly accessed: open the bucket, go to permissions and click
Editin Bucket policy section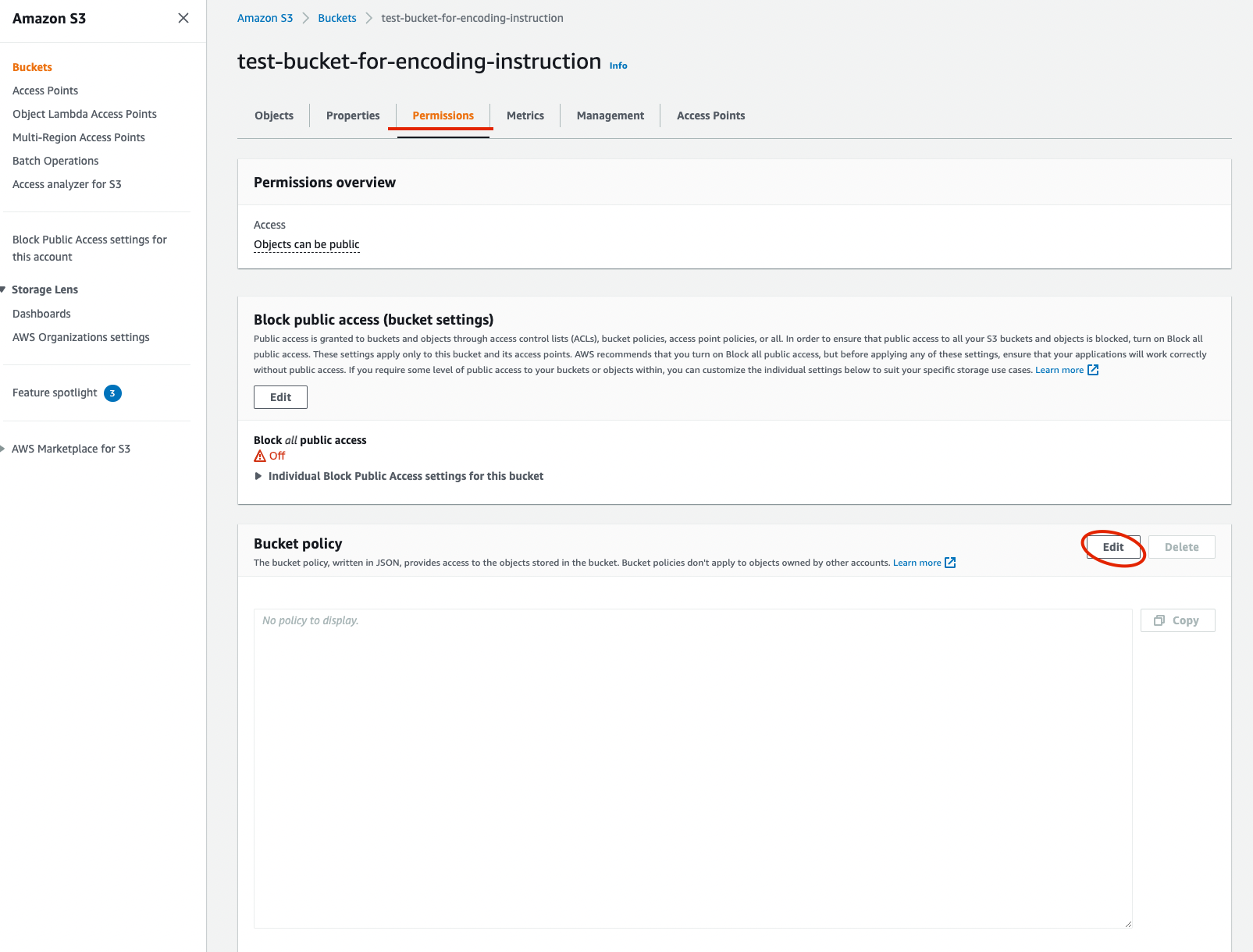 Figure 3. Bucket permissions
Figure 3. Bucket permissions -
Add a new policy. The json to be added:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "PublicReadGetObject", "Effect": "Allow", "Principal": "*", "Action": "s3:*", "Resource": "{bucket_arn}/*" } ] }Use
Bucket ARNin the Resource. And if there is no any Errors, pushSave changes.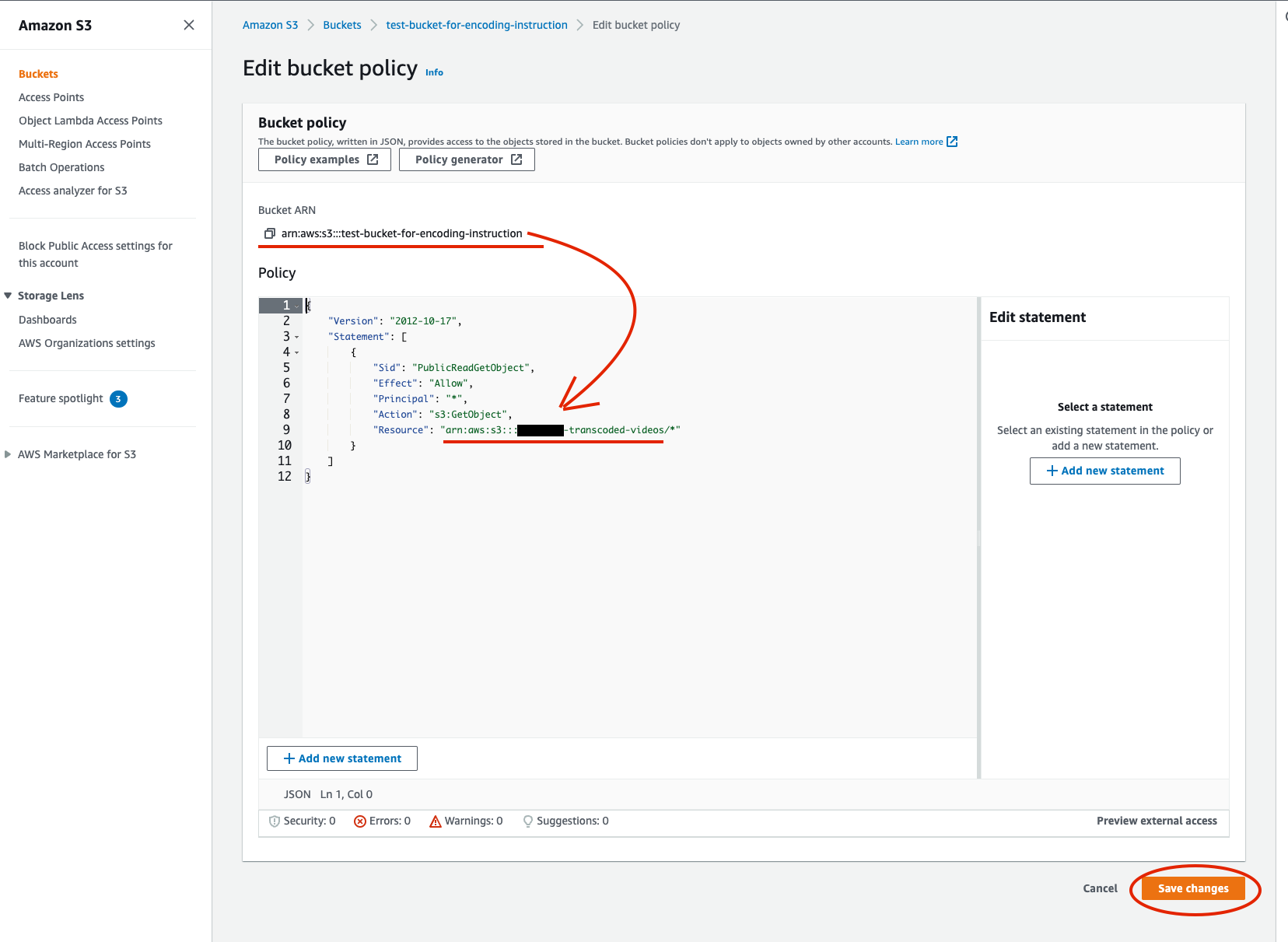 Figure 4. Bucket policy
Figure 4. Bucket policy -
As a result bucket should have Publicly accessible tag
 Figure 5. Bucket permissions
Figure 5. Bucket permissions -
To make it available for a player usage
Cross-origin resource sharing (CORS)has to be updated in the corresponded section under bucket permissions. Allowed Origins should contain list of the players URL which are ging to use the bucket. Save changes.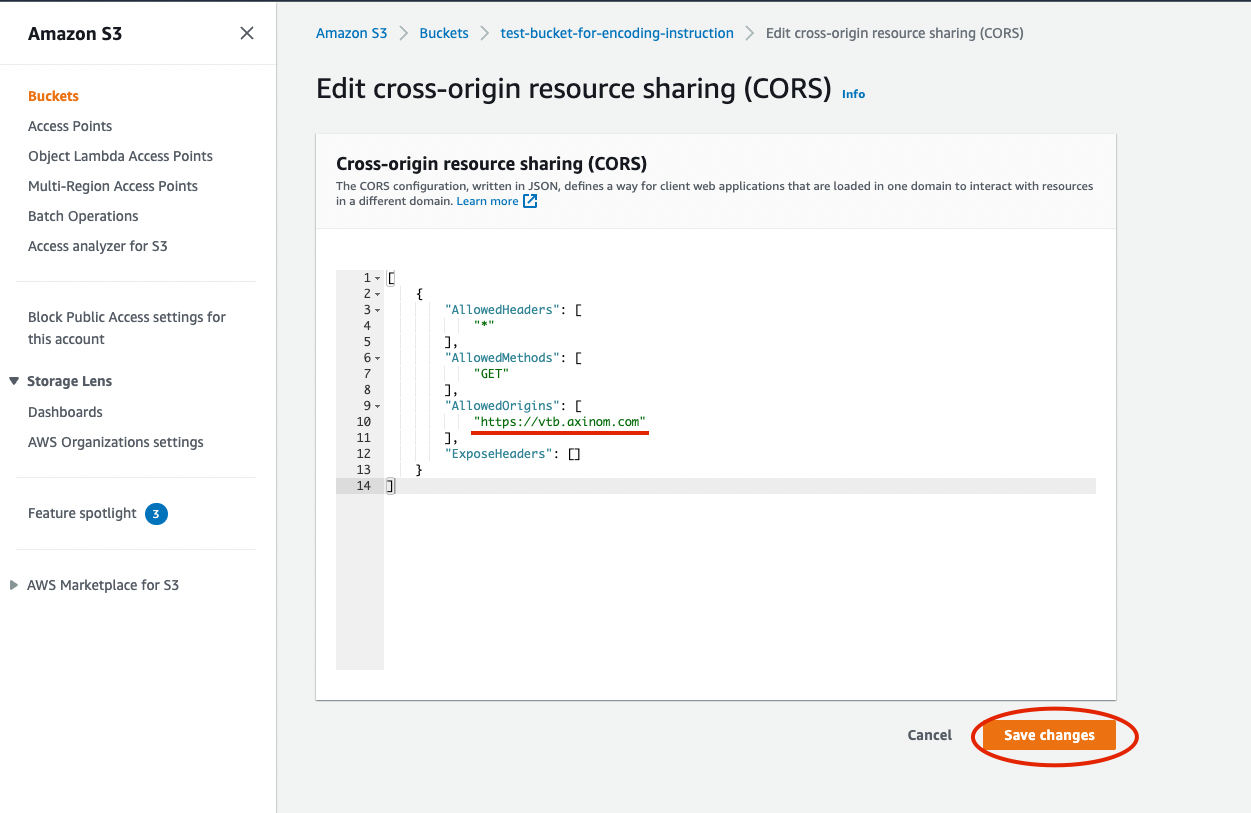 Figure 6. Bucket CORS
Figure 6. Bucket CORS -
Once the bucket is ready, additional user with correct access should be added in Amazon, which credential are needed to set up the
Acquisition Profile. Go toIdentity and Access Management (IAM)→ Users → Add users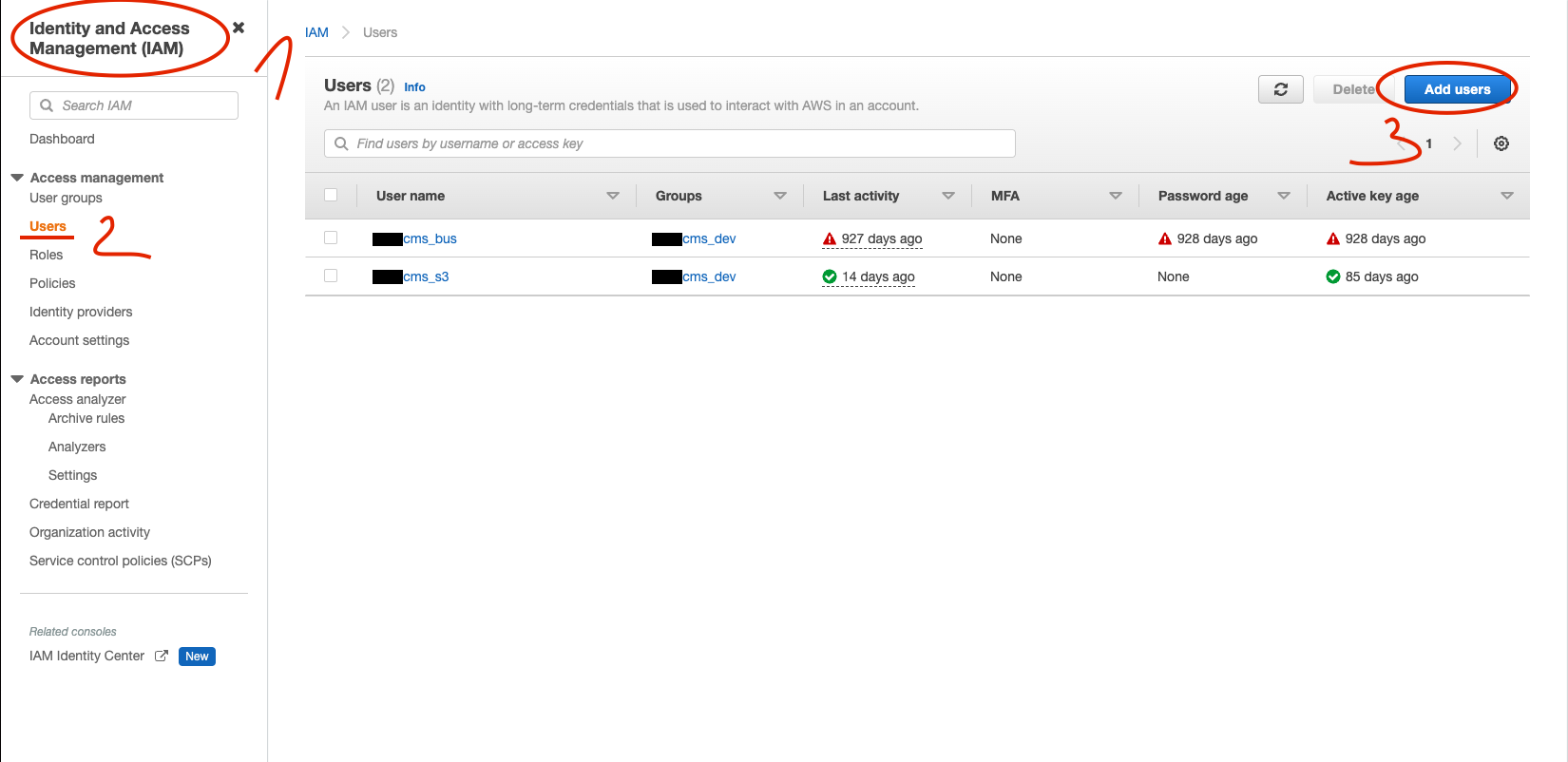 Figure 7. IAM Add User
Figure 7. IAM Add User -
Create User with proper permissions. Type User name and select
Access key - Programmatic access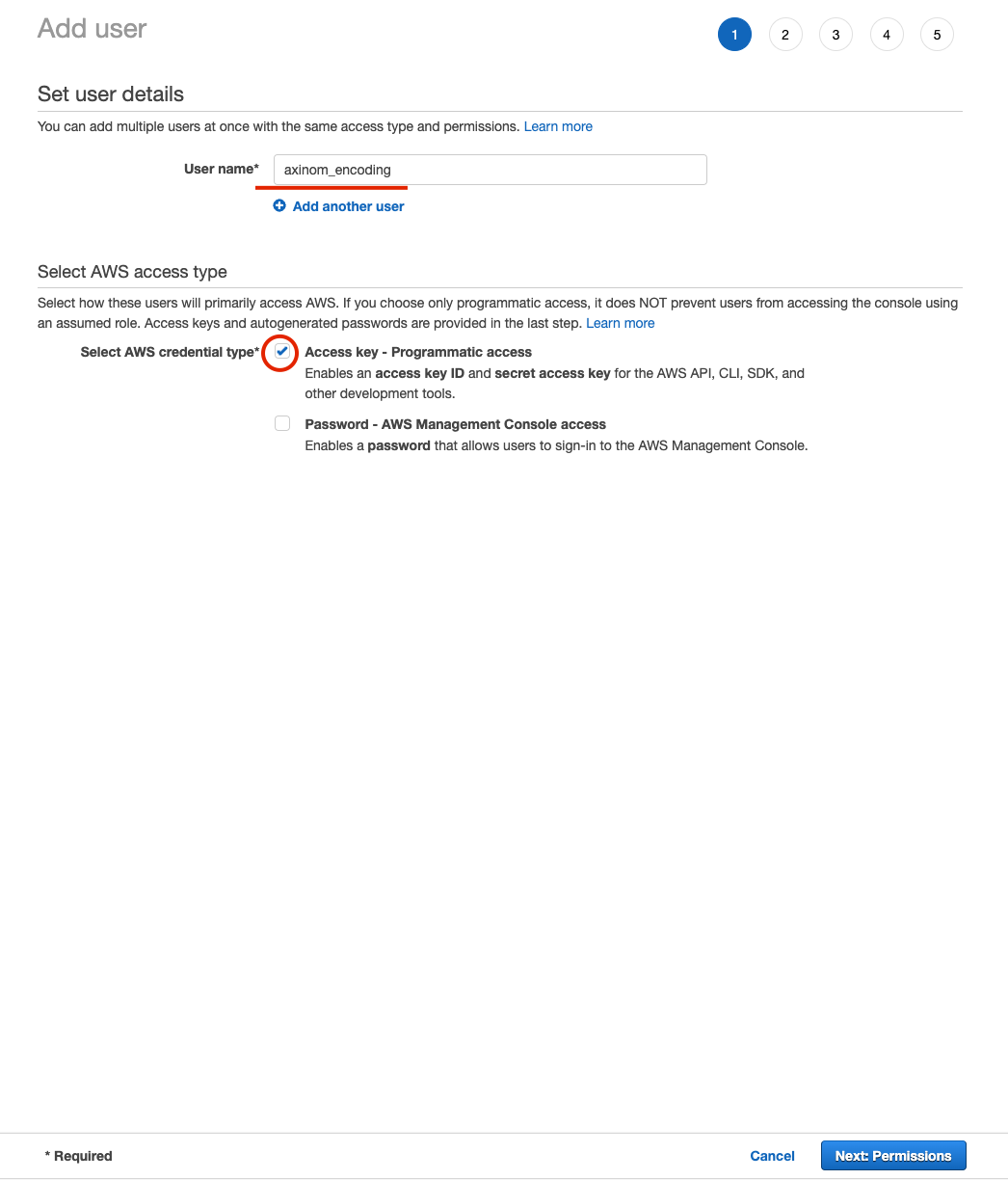 Figure 8. IAM Set user details
Figure 8. IAM Set user detailsSet permissions to the user by `Attach existing policies directly`and then Create policy
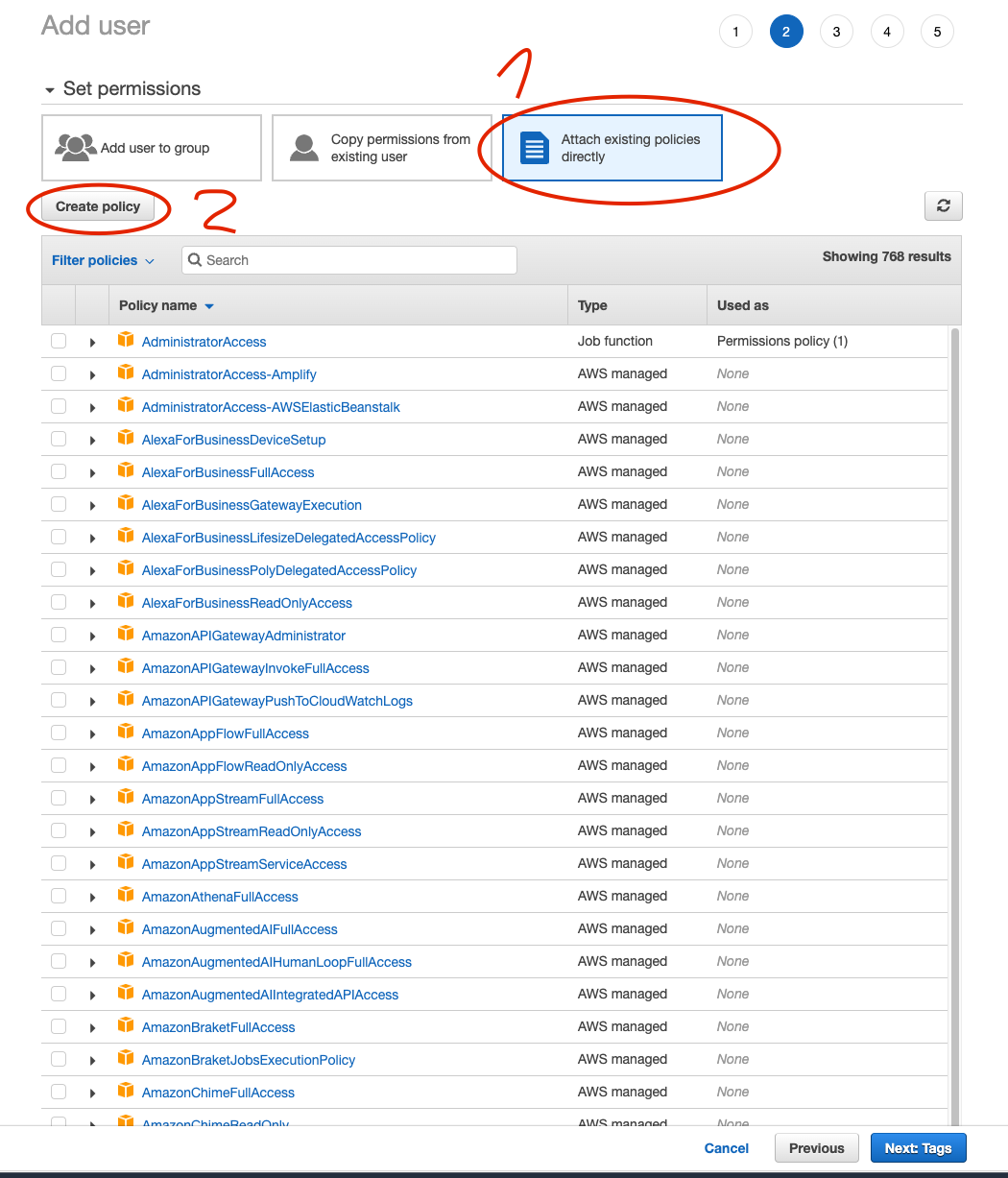 Figure 9. IAM Create Policy
Figure 9. IAM Create PolicyUse Json editor and copy paste the object with Previously created pubic bucket name:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "AccessForEncoding", "Effect": "Allow", "Action": "s3:*", "Resource": "arn:aws:s3:::{previously_created_public_bucket_name}" } ] }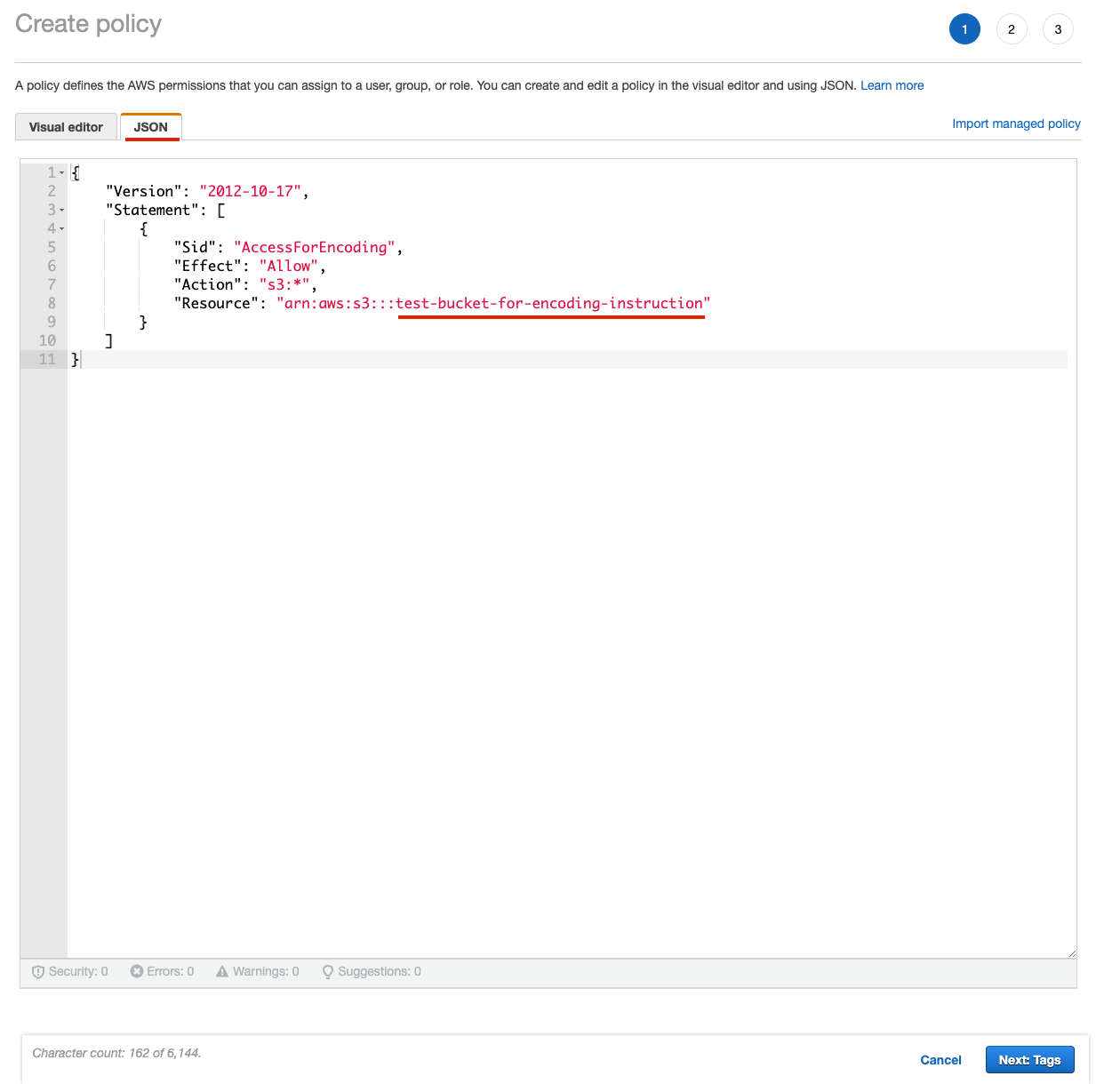 Figure 10. IAM create policy
Figure 10. IAM create policyAdd any tag if needed. We suggest adding some for the more convenient management in future.
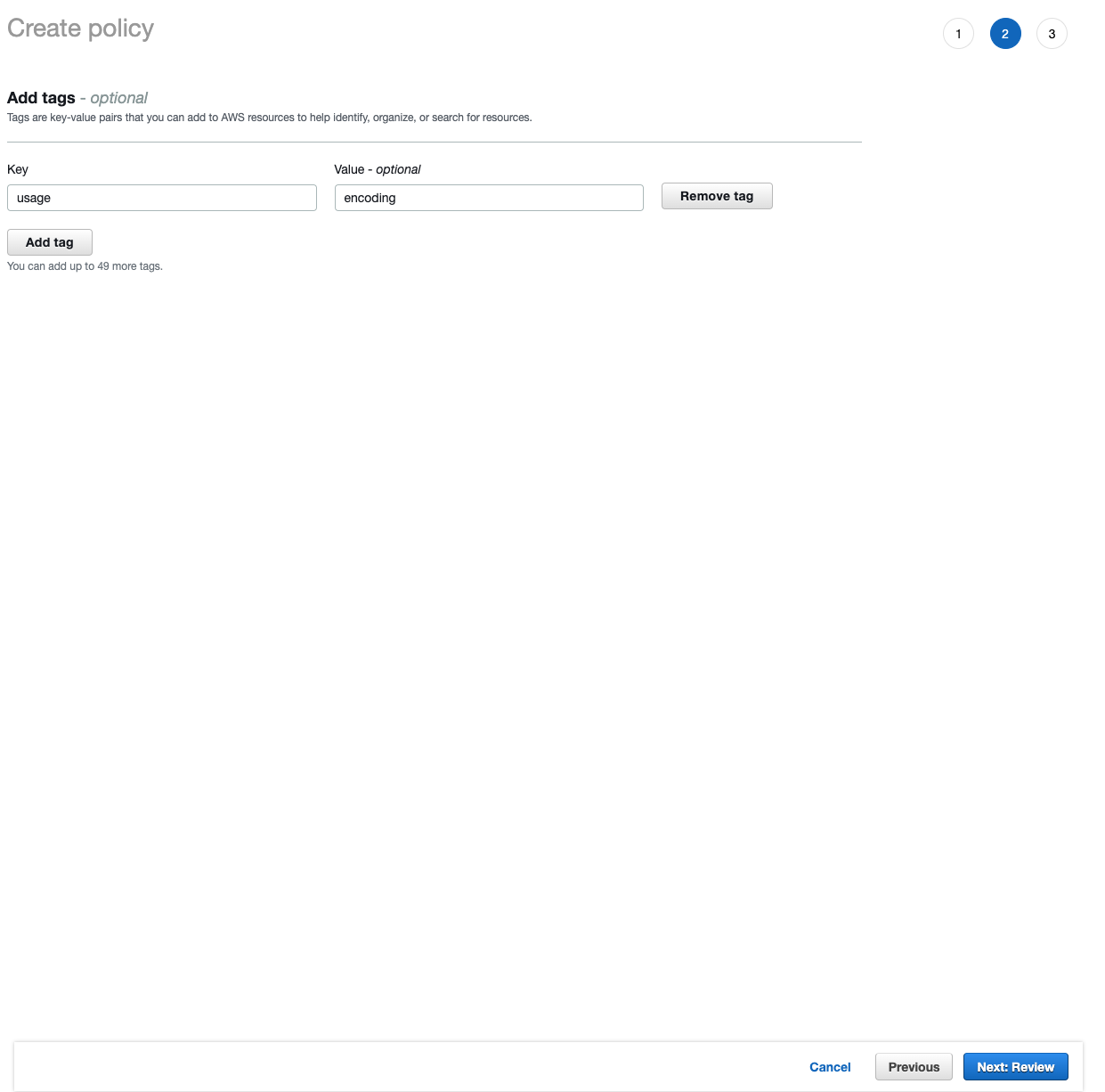 Figure 11. IAM create policy
Figure 11. IAM create policyCheck the necessary info about the new policy, name it properly (understandable name) and create a new policy. Once it’s created check that access of the policy is correct.
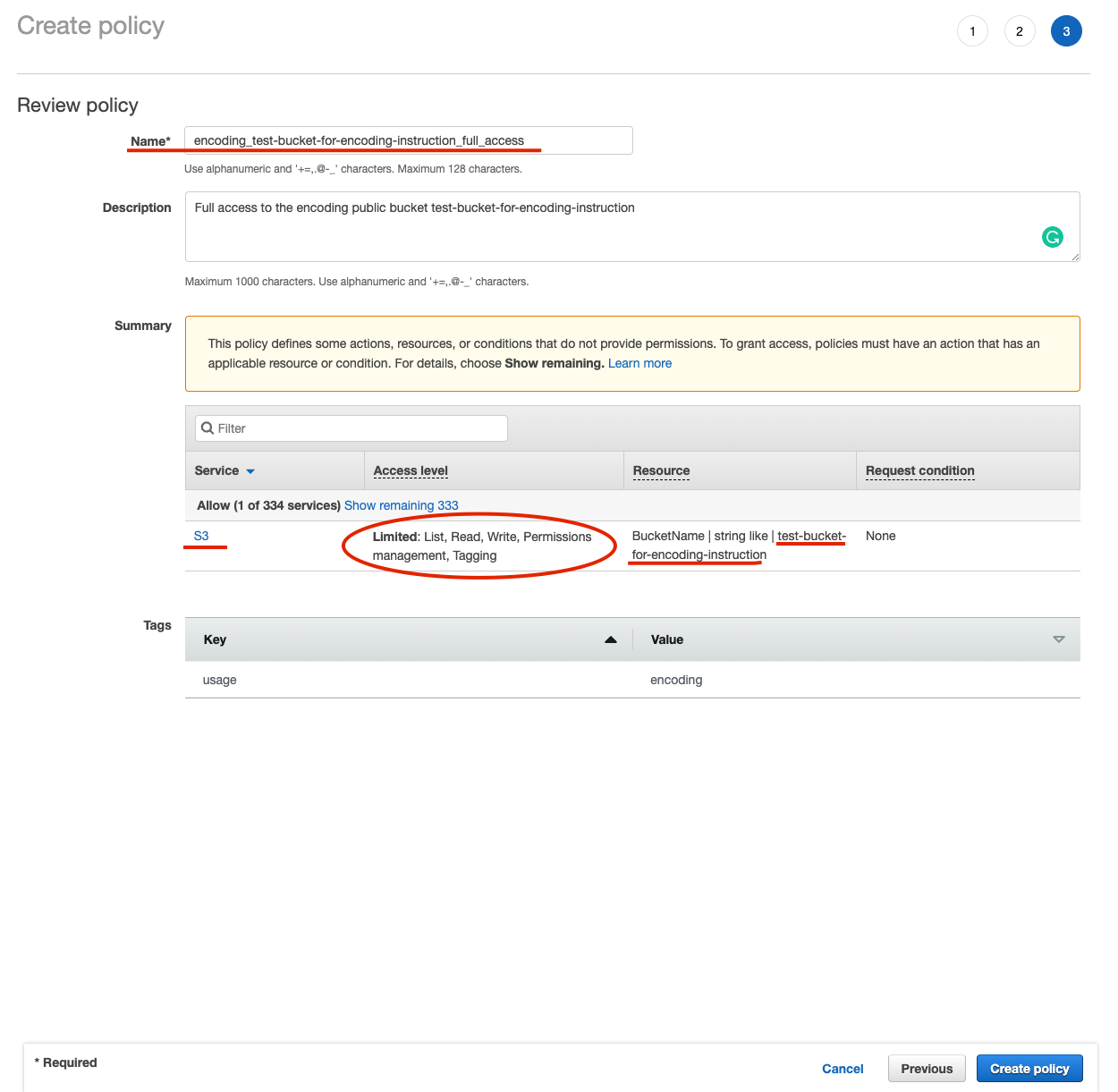 Figure 12. IAM Finish the creation
Figure 12. IAM Finish the creation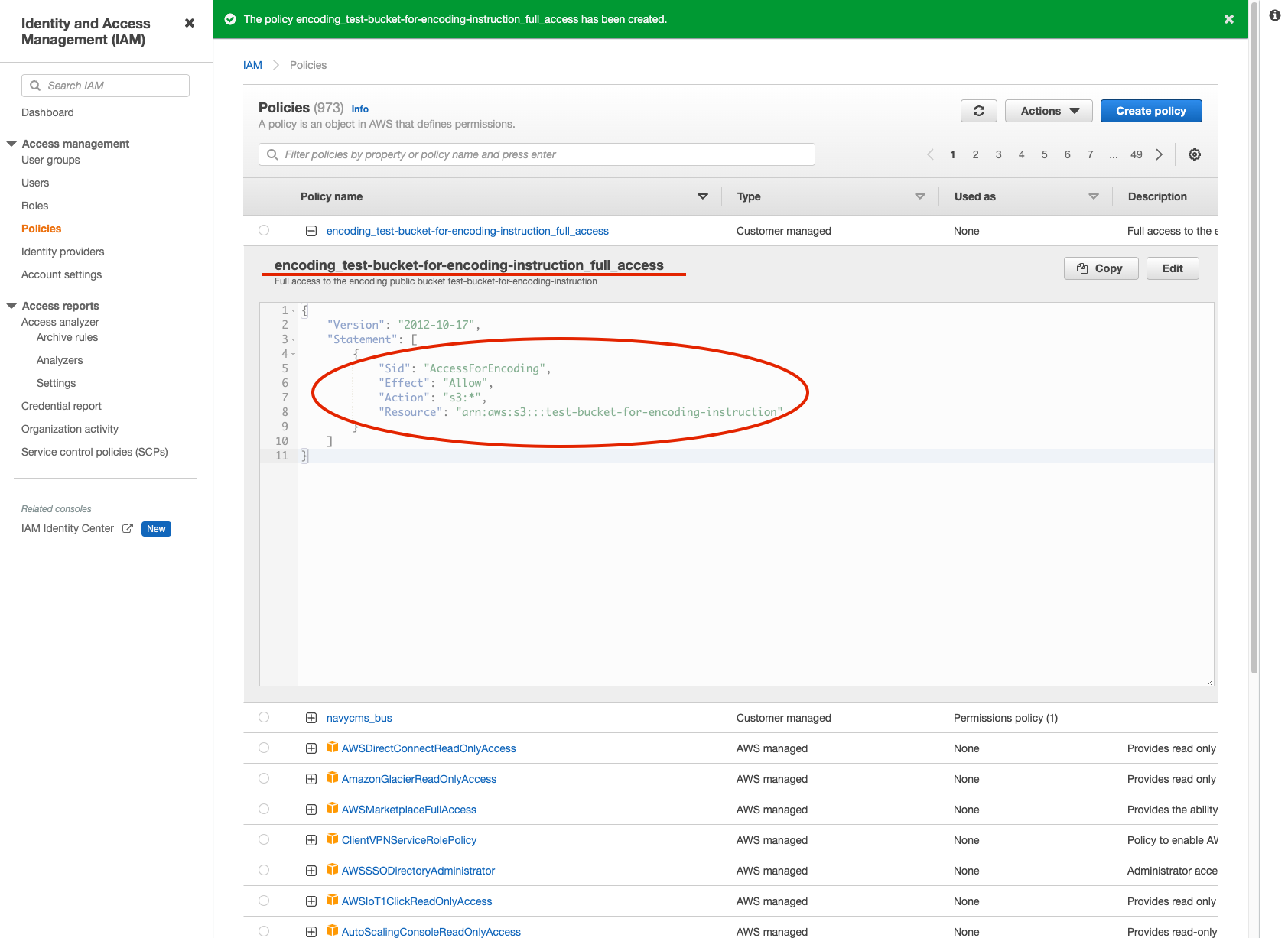 Figure 13. IAM double check the created policy
Figure 13. IAM double check the created policy -
Continue with a new user creation and select new created policy after refresh the list of locies.
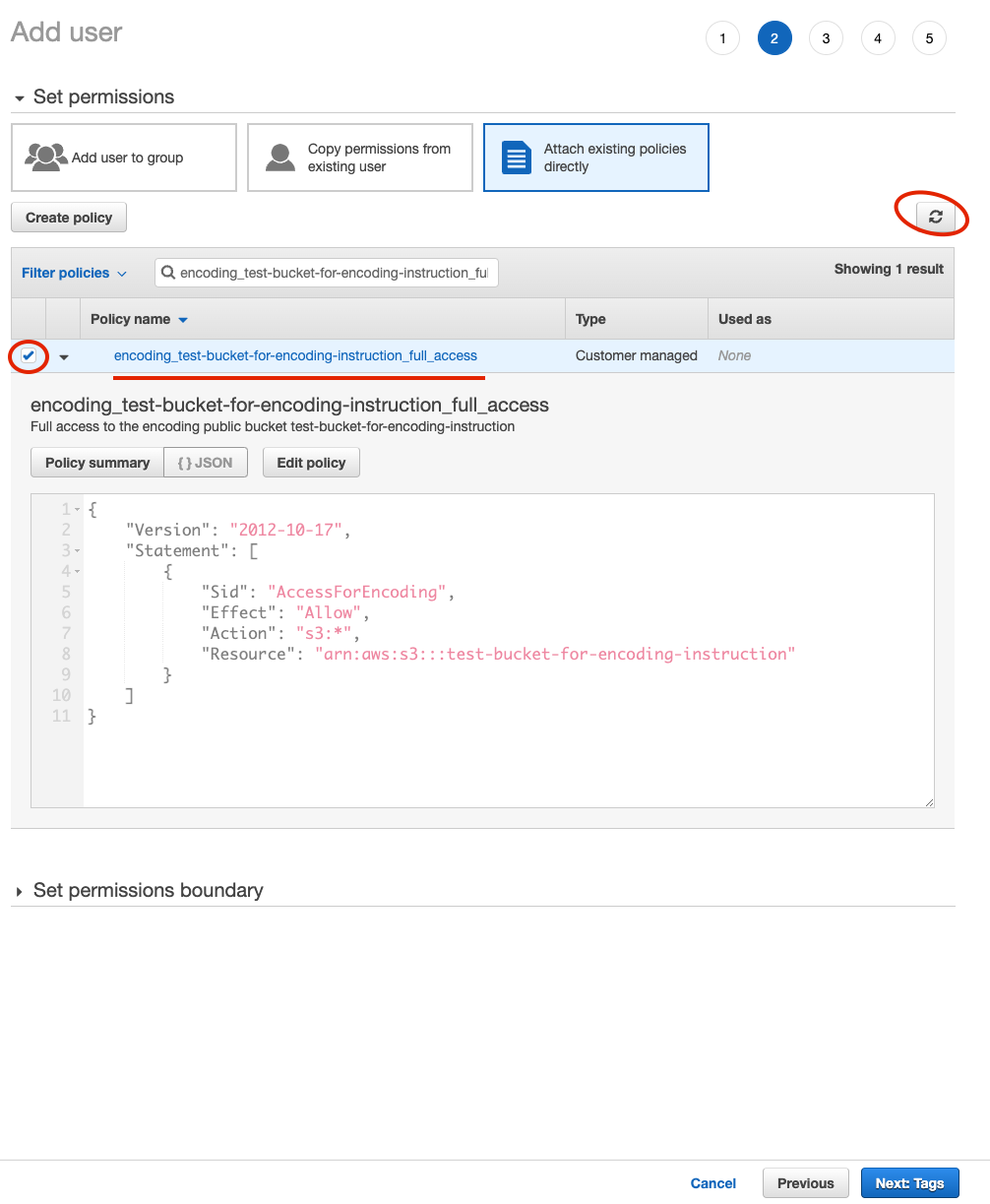 Figure 14. IAM new user select policy
Figure 14. IAM new user select policy -
Add any tag if needed. We suggest adding some for the more convenient management in future.
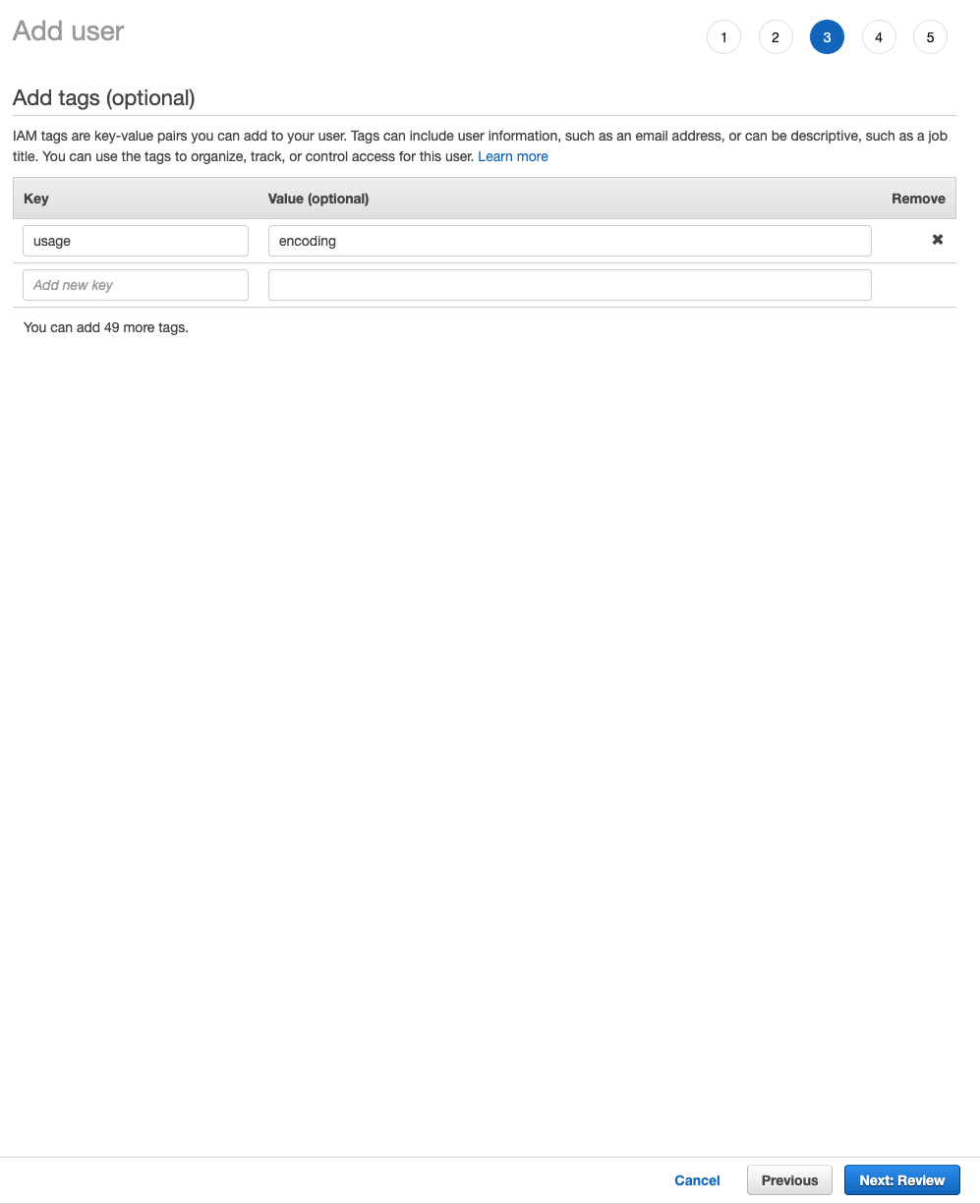 Figure 15. IAM user tags
Figure 15. IAM user tags -
Review New User and push
Create user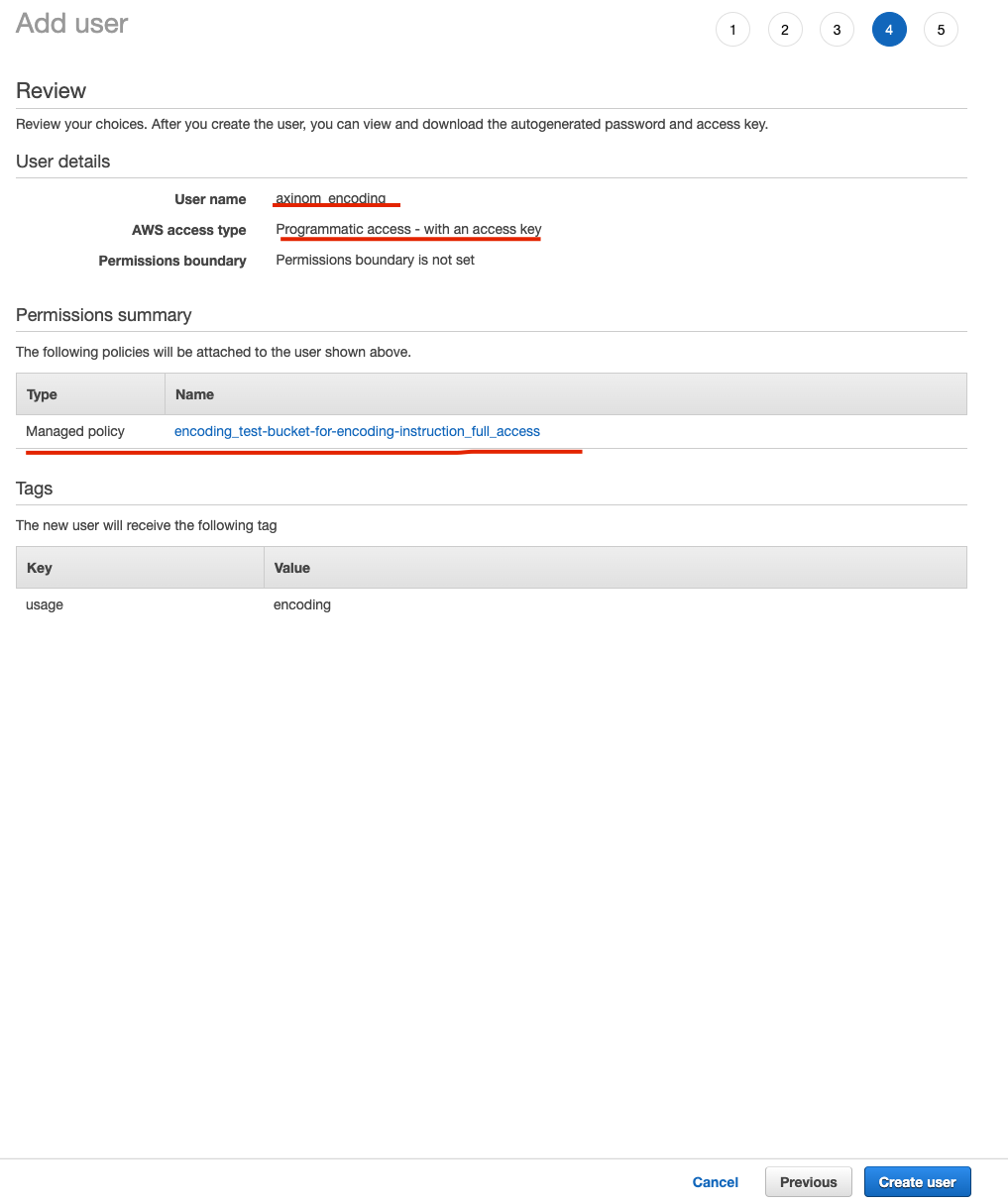 Figure 16. IAM user review
Figure 16. IAM user reviewAs a result you will get user’s credentials. Both
Access key IDandSecret access keyshould be copied and used for theAcquisition Profilesetup.ImportantSecret Access Key is not be visible once the page will be closed. Store it securely for the further usage. 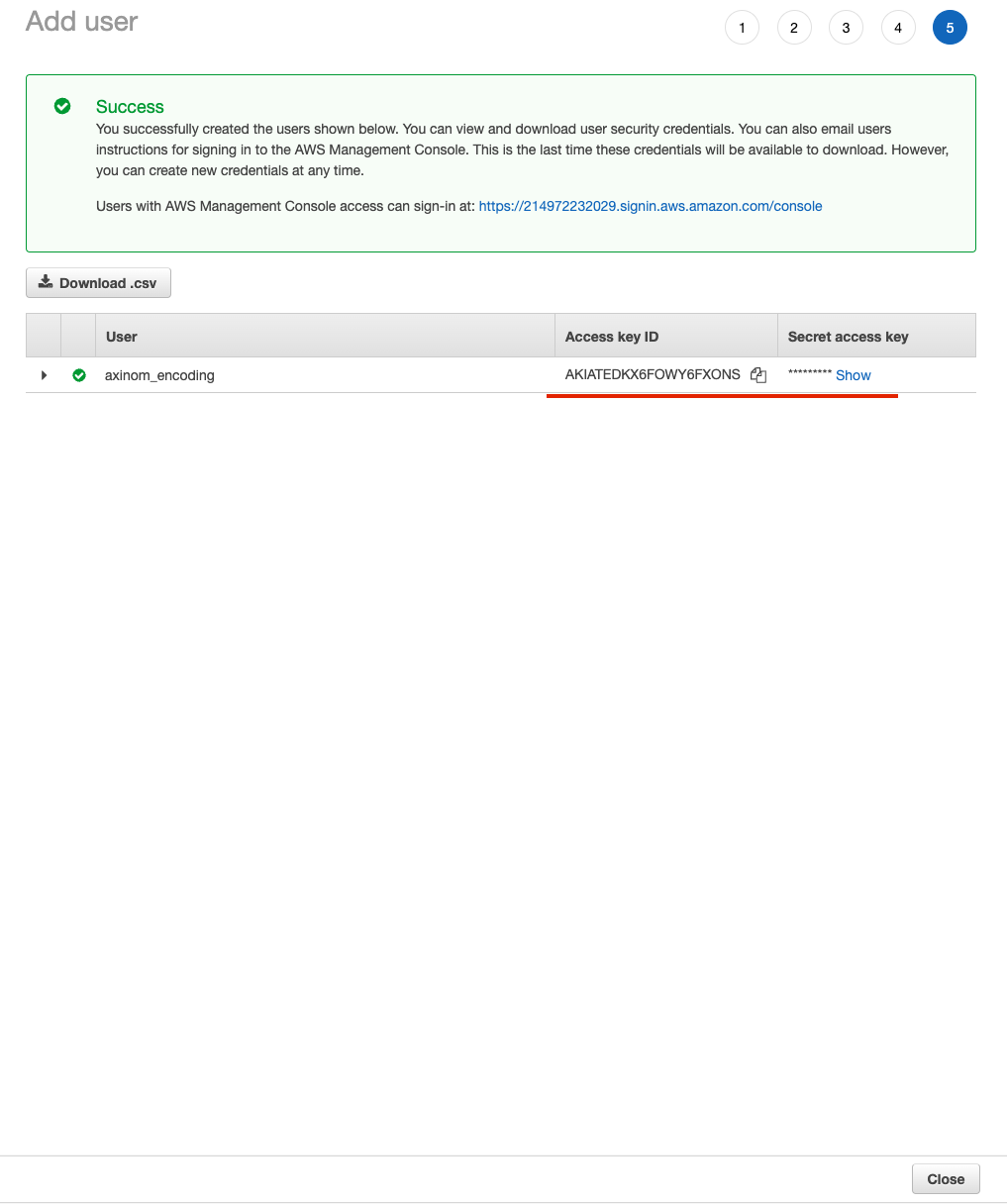 Figure 17. IAM user credentials
Figure 17. IAM user credentials

